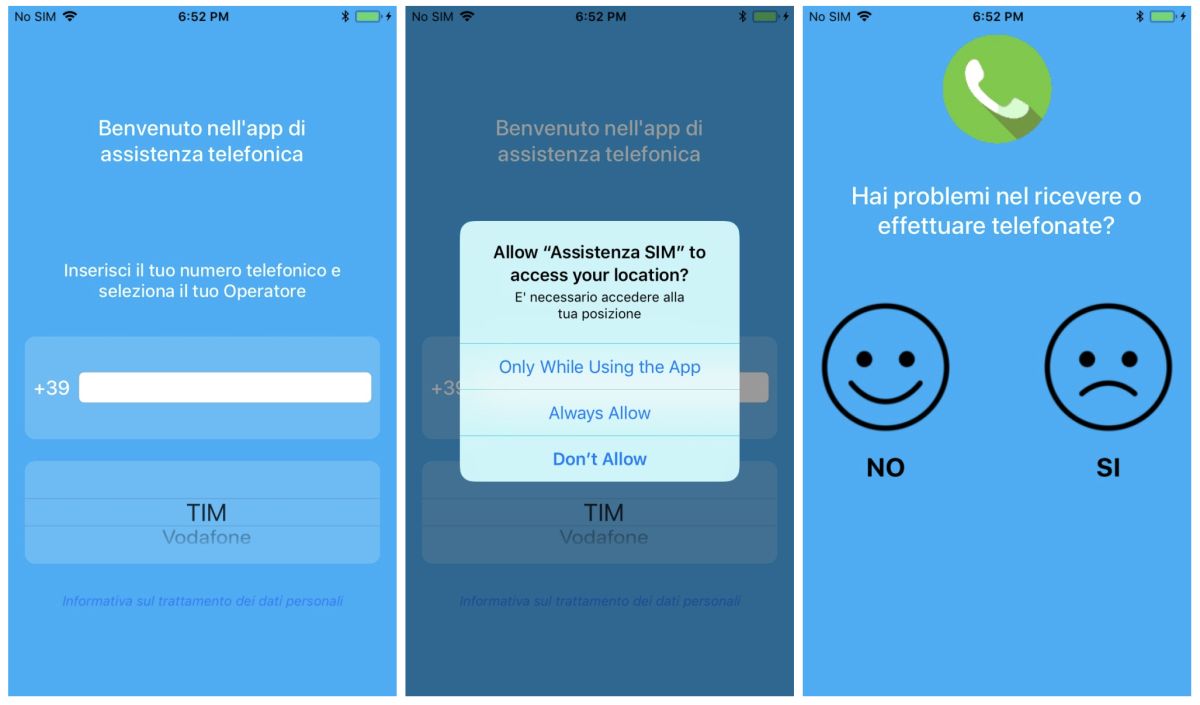
The spyware is known as Exodus, and hundreds have fall victim to the spyware simply by installing the app. Beneath the surface, Exodus contained more features and could download an additional exploit to gain root access to Android devices, granting access to sensitive data such as emails, cellular data, Wi-Fi passwords and more.
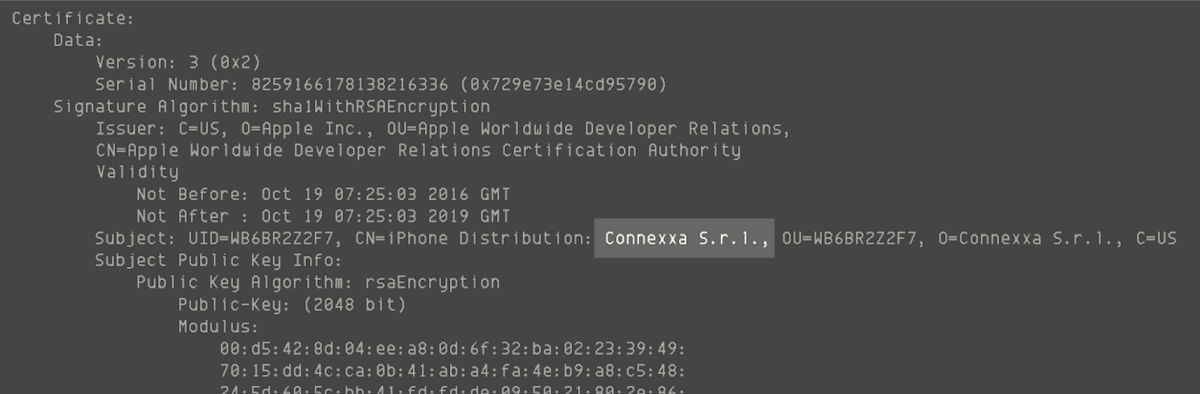
According to the report, the developers of the spyware took advantage of their Apple enterprise certificate to bypass the App Store. Once installed, the spyware collects a victim’s contacts, audio recordings, photos, videos and their real-time location data. Even worse, the attacker could even trigger the app remotely. To eavesdrop on the victim’s conversations. The researchers pointed out that the malicious app is distributed through phishing sites posing as mobile carriers in Italy and Turkmenistan. The app was eventually linked back to Connexxa, an Italian surveillance app maker.
After the researchers published their findings, Apple has revoked the enterprise certificate from Connexxa and the spyware has since been removed from both the App Store and Google Play Store. (Source: Lookout, TechCrunch, Security Without Borders // Image: TechCrunch)