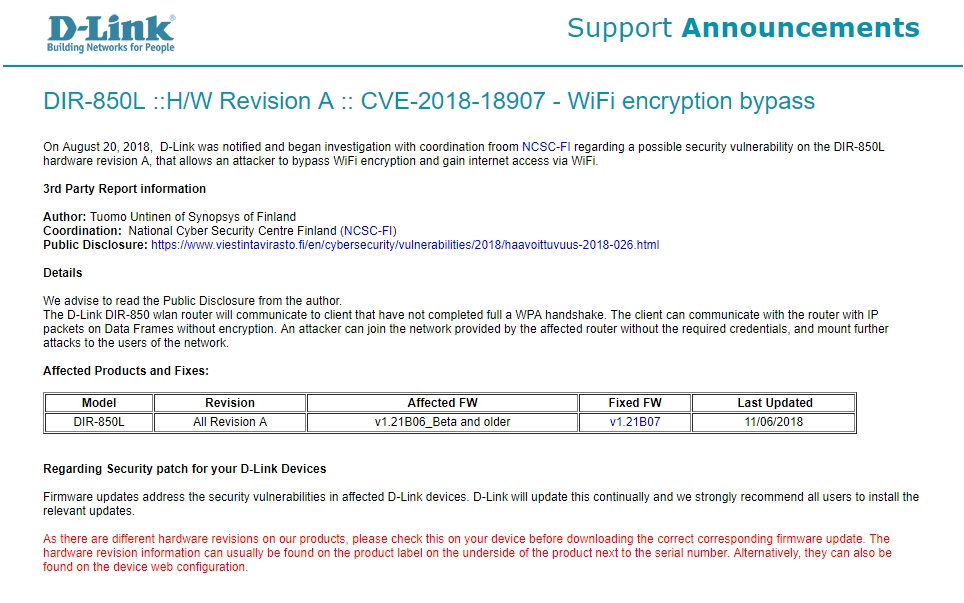
ORIGINAL STORY (200PM): The D-Link DIR-850L is one of the most popular routers being used in Malaysia, not because its a fantastic piece of hardware, but because two major ISP’s in Malaysia, TM and TIME have been providing it for free with their fibre broadband packages. While TIME has since switched to providing their new customers with TP-Link’s AC 1200 router, older customers are still stuck with the somewhat dated DIR-850L. As for TM, last we checked, even new customers are still being assigned the DIR-850L. The DIR-850L however is not a stranger to vulnerabilities. Last year, a number of critical security issues was discovered with the router, that included backdoor access to the router, as well as weak credential storage on the device itself. These were critical issues that was solved by a firmware update released by the individual ISP’s late last year. Unfortunately, it looks like that was not the end of it. On August 20th 2018, D-Link was made aware of a security vulnerability with the DIR-850L with Hardware Revision A, that allows an attacker with sufficient knowledge of the issue to bypass WiFi encryption (inclusive of WPA) and gain internet access without any credentials. The D-Link DIR-850L with Hardware Revision B is not affected. D-Link confirmed the vulnerability on the 6th of November 2018, and released a firmware update to address the issue. However, similar to the incident last year, TIME and unifi users will not be able to patch their devices using the generic firmware released by D-Link. If your DIR-850L was provided by your ISP, then you will need to wait for D-Link Malaysia, or the respective ISP’s to roll out their customized firmware update. At time of writing, neither D-Link Malaysia, TIME Internet or Telekom Malaysia has issued any update or advisories on this security vulnerability, or when a firmware update will be made available.
Temporary Solutions
While this particular vulnerability doesn’t exactly allow someone to infiltrate your network from anywhere around the world, it does open your network up to someone within your Wi-Fi range to have unrestricted access to your Wi-Fi internet connection, as well as files within your local network that the router is connected to. Turning off your Wi-Fi and switching to a wired connection until a firmware update is a simple solution to avoid your data or network being compromised at this point in time. Alternatively, for under RM100, you should be able to get a decent replacement router in the market. We will update this story once we receive more information from D-Link Malaysia, or any of the affected ISP’s. (Source: Synopsys’ Cybersecurity Researcher Tuomo Untinen, Finland)